DIGITAL.CLOUD.READY.
ZERO TRUST NETWORK ACCESS.
a zero trust security model will be key to your digital transformation
Enhancing your security posture and protecting your digital cloud with zero trust to meet the demands of today’s complex environments.

- Protect and empower your people and digital infrastructure with a Zero Trust architecture.
- Seamless, fast and secure connectivity to your digital applications allowing your people to work from anywhere.
- Ensure your people are as secure on the internet as they would be on your corporate network.
- Secure all your digital applications whether on-prem, hybrid or pure cloud.
Zero Trust: background
Zero trust is a concept first identified by John Kindervag at Forrester Research more than a decade ago. It is a framework for enabling certain capabilities that secure organizations in the modern cloud and mobile world. A key principle of zero trust is least-privileged access, which assumes that no user or application should be inherently trusted. Instead, trust is established based on the user identity and context (such as the user’s location, the security posture of the endpoint, and the app or service being requested) with policy as the gatekeeper every step of the way. With more mobile users connecting unmanaged devices to business applications over the internet, there’s a growing need for zero trust security. When you can’t trust the connection, device, or network, zero trust sounds like a great idea, but it’s difficult to implement effectively without being absolutely clear on what the term “zero trust” actually means. So, let’s be clear.
Zero trust is a cybersecurity strategy wherein security policy is applied based not on assumed trust, but on context established through least-privileged access controls and strict user authentication. A well-tuned zero trust architecture leads to simpler overall network infrastructure, a better user experience, and ultimately improved protection against cyberthreats.
An architecture based on zero trust follows the maxim “never trust,” always verify.” It enforces access policies based on specific context—including the user’s role and location, their device, and what data they are requesting—to block inappropriate access and lateral movement throughout a data environment. Establishing an effective zero trust architecture requires visibility and control over the environment’s users and traffic, including that which is encrypted; monitoring and verification of traffic between parts of the environment; and strong multifactor authentication methods beyond passwords, such as biometrics or one-time codes.
Customised
access policy for users and their
devices
When all employees have the same access permissions and those permissions grant full network access, the attack surface is wide and vulnerabilities abound. ZTNA enables you to segment your network and narrow access rules to individual users and groups, with authentication enforced via identity providers.
Zero Trust and digital modernisation
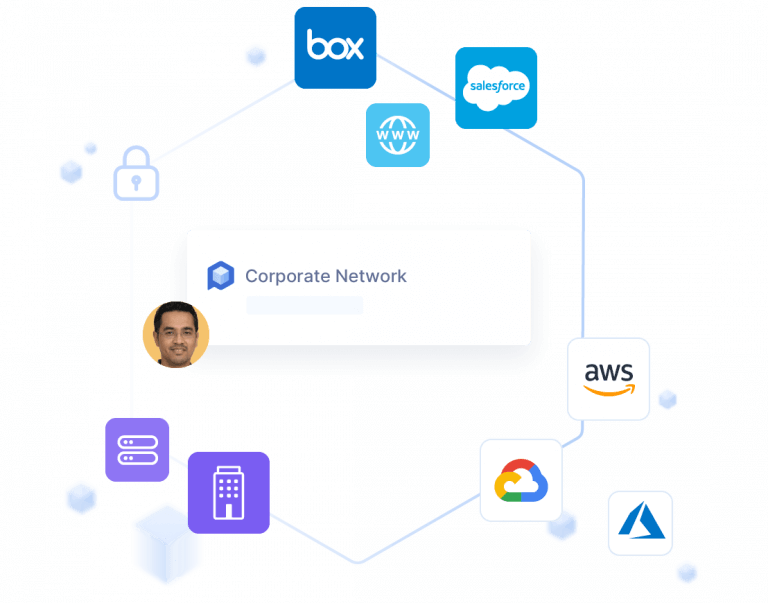
At its core, the concept of zero trust is simple: assume everything is hostile. While this sounds obvious, the notion is antithetical to the corporate network security model built on the centralized data center and the secure network perimeter. Since the early 1990s, companies have been building a network architecture with a secure perimeter using endpoint-based controls, relying on approved IP addresses, ports, and protocols to establish access controls and validate applications, data, and/or users, which are then trusted to communicate inside the network. In this model, users outside the secure perimeter used VPNs to establish remote access to the internal network, and they were trusted once inside.
In contrast, the zero trust approach treats all traffic, including traffic already inside the perimeter, as hostile. For example, unless workloads have been identified by a set of attributes—a workload fingerprint or identity—they are untrusted and blocked from communicating. Identity-based policies result in stronger security that travels with the workload wherever it communicates—in a public cloud, a hybrid environment, a container, or an on-premises network architecture. Because protection is environment-agnostic, applications and services are secured using a zero trust approach even if they communicate across network environments, requiring no architectural changes or policy updates.
In the simplest terms, zero trust securely connects users, devices, and applications using business policies over any network.
Integrate
security into every
environment
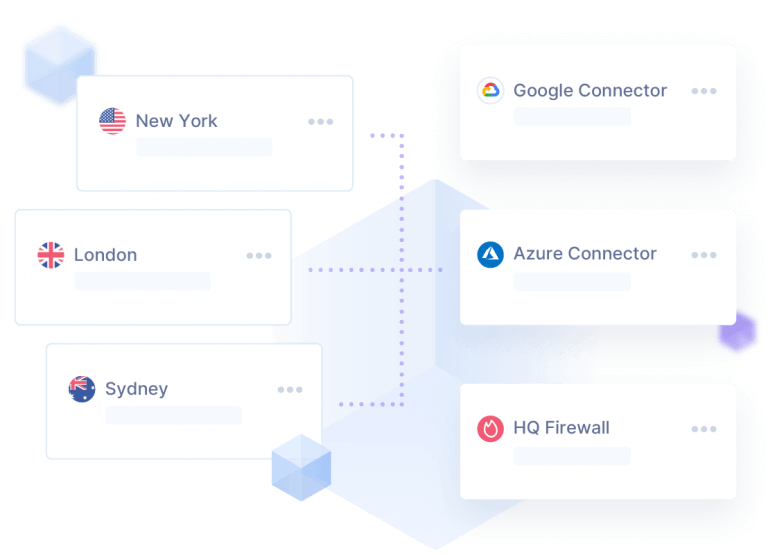
When their companies rely heavily on the cloud, and encourage remote work and BYOD, a primary concern for IT is complexity and reduced visibility into network activity and access. Perimeter 81 integrates with all your various solutions and services for total network awareness.
Achieving Zero Trust
Zero trust is not simply about a single technology such as user identity, remote user access, or network segmentation. Zero trust is a strategy, a foundation upon which to build a cybersecurity ecosystem. At its core are three tenets:
- Terminate every connection: Many technologies, such as firewalls, use a “passthrough” approach, which means that files are sent to their recipients at the same time they’re being inspected.
If a malicious file is detected, an alert is sent, but it can often be too late. In contrast, zero trust terminates every connection so it can hold and inspect unknown files before they reach the endpoint. Built on a proxy architecture,
zero trust operates inline and inspects all traffic at line speed, including encrypted traffic, executing deep data and threat analysis.
- Protect data using granular policies based on context: Zero trust applies user identity and device posture to verify access rights, and it uses granular business policies based upon context,
including user, device, the application being requested, as well as the type of content. Policies are adaptive, which means that as context changes, such as the user’s location or device, the user access privileges are continually
reassessed.
- Reduce risk by eliminating the attack surface: Zero trust connects users directly to the applications and resources they need, and never connects them to networks. By enabling one-to-one connections (user-to-app and app-to-app), zero trust eliminates the risk of lateral movement and prevents a compromised device from infecting other network resources. With zero trust, users and applications are invisible to the internet, so they can’t be discovered or attacked.
Increase
application
availability for remote workers
Now that the traditional network perimeter is gone and access occurs further away from network resources, it’s time to bring resources closer to where they’re needed. Private network gateways limit latency and boost speeds for productive and agile remote work no matter where your employees are located.
Reasons to adopt Zero Trust
Today’s cloud environments can be hostile places. They host business-critical applications and data, making them ripe for attack by hackers who would like nothing more than to steal, destroy, or hold hostage sensitive data, such as personally identifiable information (PII), intellectual property (IP), and financial information for personal gain.
While no security strategy is perfect, and data breaches will never be totally eliminated, zero trust reduces the attack surface and limits the blast radius – that is, the impact and severity – of a cyberattack, which reduces the time and cost of responding to and cleaning up after a data breach.
USEFUL REFERENCES
Gartner
Market Guide for Zero Trust Network Access
Forrester
New Wave Report: Zero Trust Network Access
Cyber Security Insiders
Zero Trust Adoption Report
Privacy Affairs
Zero Trust Network Access: A Complete Guide
Get in touch
We’d love to hear from you, so please feel free to get in touch with us via phone, email or this contact form.
